These days, there isn’t really an excuse to not protect all the things with some form of encryption. If your web server supports it – and most either do or have workarounds – you should at the very least employ a free Let’s Encrypt certificate. If you have Tableau Server, the couple hundred bucks every other year to renew your certificate is most likely not a barrier.
But what about the renewal process? What if you could automate that? What if it was free? What if you could do this on both Windows and Linux? Well, you can. Here are some basic steps to get your Windows Tableau Server running with a free, auto-renewing SSL certificate from Let’s Encrypt.
Pick a Client … but Not Just Any Client
The standard for Let’s Encrypt is certbot, but if you are on Windows, certbot has no love for you. Luckily, Let’s Encrypt has a page dedicated to a list of alternative clients, including those for Windows. I ended up going with ZeroSSL because their GitHub is active and they provide standalone binaries for Windows with plenty of CLI options to get your sweet SSL automation up and running. No need to build anything, just head over to their GitHub page and download the latest release of either le32.zip or le64.zip. If you live in a world of paranoia, they also provide the source for you to inspect, build on your own or extend/integrate with whatever you like.
Let’s Get This (SSL) Party Started
Here is how I would set this up on a typical Tableau Server:
Create/designate folders for your account.key, CSR, domain key, domain certificate, logs, le64.exe and scripts. We recommend the following:
- D:\scritpts\le for account.key, CSR, logs, le64.exe and scripts
- D:\<Tableau Install Path>\Tableau Server\ssl\ for domain key and certificate
Generate your account key. You can do this in advance or let le64.exe do it for you. The recommended practice is to generate it in advance using OpenSSL if available:
openssl genrsa -out account.key 4096
Build your command to generate and issue your domain key and certificate:
le64.exe --key d:\scripts\le\account.key --csr d:\scripts\le\my.tableauserver.com.csr --csr-key "D:\Program Files\Tableau\Tableau Server\ssl\my.tableauserver.com.key" --crt "D:\Program Files\Tableau\Tableau Server\ssl\my.tableauserver.com.crt" --domains "my.tableauserver.com" --generate-missing --handle-as dns --live
- –key: Path to your account key.
- –csr: Path to where you want to generate your CSR.
- –csr-key: Path to where you want your domain key to be stored. Our standard is an SSL folder in the Tableau Server directory.
- –crt: Path to where you want your domain certificate to be stored. Same logic as –csr-key.
- –domains: What domain(s) are you protecting with this certificate. Probably only need one here.
- –generate-missing: Directs le64.exe to create keys and CSR if they do not already exist in the paths specified.
- –handle-as dns: Directs le64.exe that you will be verifying domain verification using the DNS method. After running, it will give you instruction on adding a TXT record to your public DNS.
- –live: You can omit this to test that your command is working before actually generating a certificate.
After running the command and verifying domain ownership, you should have a certificate and key ready to use with your Tableau Server. The certificate contains both the issued certificate and the intermediate, giving you a complete chain. Fire up your Tableau Server configuration and enable SSL using your new key and certificate.
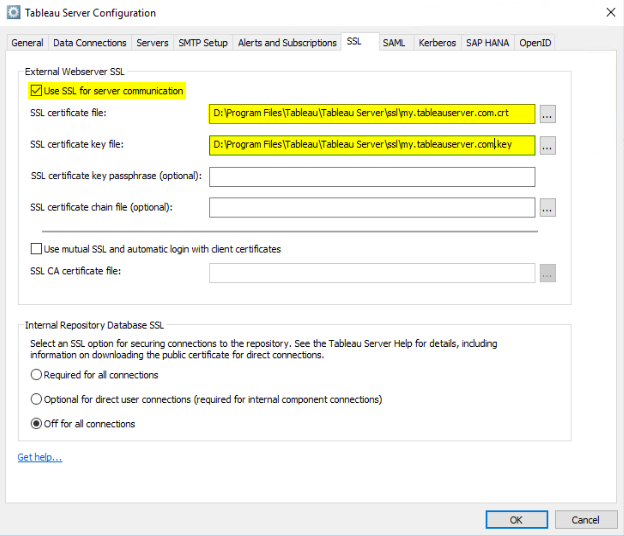
Save and restart Tableau Server. Once services are back up and running, you should now have HTTPS enabled with HTTP redirecting to HTTPS. You can view more details and verify that your certificate chain is set up correctly by using a tool like SSLDecoder.
Automate This
Here is a script you can use to automate renewals. Save the following as a .bat file.
rem Logging Enabled le64.exe --key d:\scripts\le\account.key --csr d:\scripts\le\my.tableauserver.com.csr --csr-key "D:\Program Files\Tableau\Tableau Server\ssl\my.tableauserver.com.key" --crt "D:\Program Files\Tableau\Tableau Server\ssl\my.tableauserver.com.crt" --domains "my.tableauserver.com" --generate-missing --renew 10 --issue-code 100 --log-config D:\scripts\le\log.config --handle-as dns --live rem Logging NOT enabled rem le64.exe --key d:\scripts\le\account.key --csr d:\scripts\le\my.tableauserver.com.csr --csr-key "D:\Program Files\Tableau\Tableau Server\ssl\my.tableauserver.com.key" --crt "D:\Program Files\Tableau\Tableau Server\ssl\my.tableauserver.com.crt" --domains "my.tableauserver.com" --generate-missing --renew 10 --issue-code 100 --log-config D:\scripts\le\log.config --handle-as dns --live if errorlevel 100 ( "D:\Program Files\Tableau\Tableau Server\2018.1\bin\tabadmin" restart ) if not errorlevel 100 ( echo "Something went wrong. Is it time to renew yet? (<=10 days prior to renewal)" )
- –renew 10: Directs le64.exe to renew when the certificate has 10 or fewer days remaining until expiration.
- –issue-code 100: Arbitrary return code you can use to detect when a renewal has occurred. You can take action, such as restarting Tableau Server and, if clustered, copying the new cert and key to other worker nodes, which is required when your certificate is updated.
- –log-config: Path to log.config containing log4perl settings needed to output a log file. Optional but useful in troubleshooting. The default log.config settings can be found here.
- –hand-as dns: It’s important to leave the DNS record that you created for the initial certificate in your public DNS as renewals will use the same record for verification. The verification string is tied to your domains list and account.key. If either change, you will be re-prompted with a new DNS string for verification.
Schedule with Windows Task Scheduler:
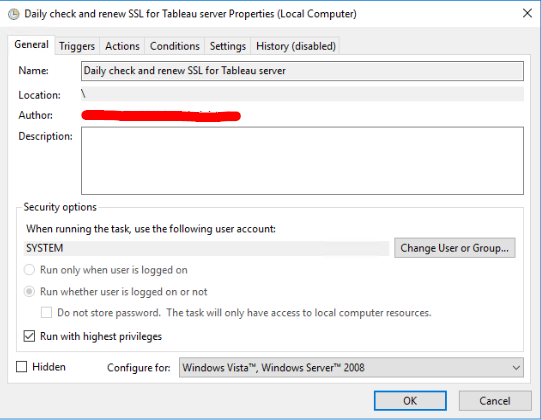
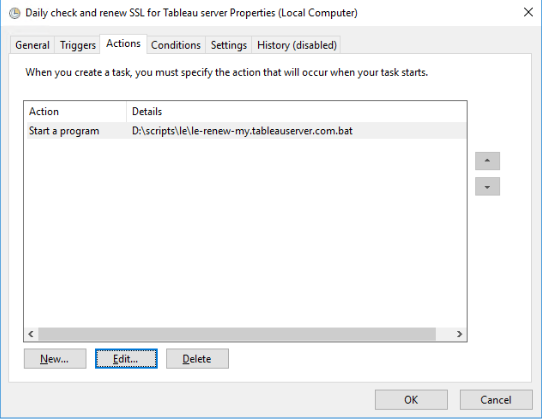
Run it once to make sure it works. You should see the following in your log file:
2018/08/28 00:00:02 [INFO] [ ZeroSSL Crypt::LE client v0.31 started. ] 2018/08/28 00:00:02 [INFO] Loading an account key from d:\scripts\le\account.key 2018/08/28 00:00:02 [INFO] Loading a CSR from d:\scripts\le\my.tableauserver.com.csr 2018/08/28 00:00:02 [INFO] Checking certificate for expiration (local file). 2018/08/28 00:00:02 [INFO] Too early for renewal, certificate expires in 89 days.
What if I Have a Cluster?
Simply add a step to your automation that copies the certificate and key to your workers. Since architecture and security can vary greatly, I won’t post a script for this. I’ll leave it to you to build this out appropriately based on your own requirements.
Hint: Run your code to copy to workers before restarting Tableau Server. The main requirement is that the key and certificate exist in the exact same path as your primary server, such as: “D:\Program Files\Tableau\Tableau Server\ssl\”
The post Protect Tableau Server for Free with Let’s Encrypt (Windows) appeared first on InterWorks.